🚀 Getting Started
This article will guide you through unusd.cloud initial setup. At this point, you are 5 minutes away from starting to save money.
Sign-up
Sign-up to unusd.cloud and setup your AWS accounts with desired configuration for reports like communication channels and scan schedule.
Add AWS Accounts
- Login to unusd.cloud backstage app
- Add each of your AWS accounts and desired report configuration (Web, Email, Slack, Microsoft Teams)
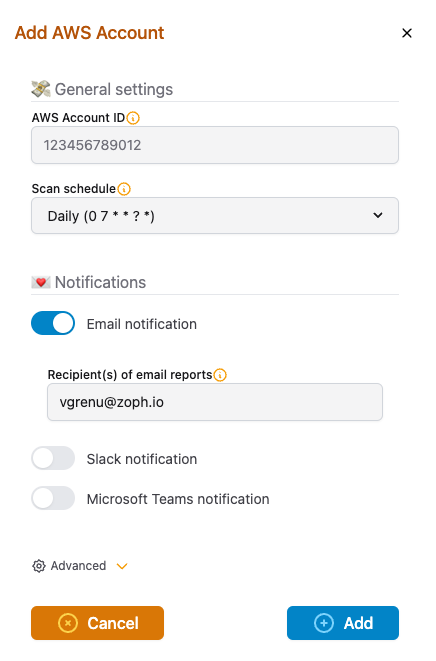
Then deploy the associated Read-only IAM Role using the provided link to CloudFormation console (Terraform available):
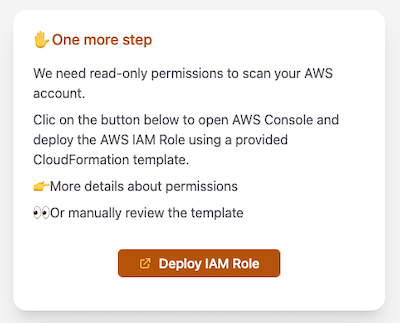
Repeat this operation, on every AWS account that you want to attach to your unusd.cloud subscription.
If you have multiple AWS accounts, prefer the usage of AWS CloudFormation StackSets feature, it will allow you to deploy the IAM Role to all your AWS accounts with a single deployment.
💡️ Read our dedicated documentation on this method.
Add Exception tag [Optional]
To prevent alert fatigue and irrelevant reports, it may be necessary to add legitimate assets to the exception list. Typically, this can be accomplished by setting an AWS tag on an existing legitimate AWS assets.
To simplify the process, you can utilize an existing AWS tag that has already been deployed to your legitimate assets. The Key of this tag is part of the unusd configuration (Exception Tag), in the advanced menu. The default tag key is unusd.