🔒 Security
The security measures employed by unusd.cloud and our data handling practices are detailed in this page.
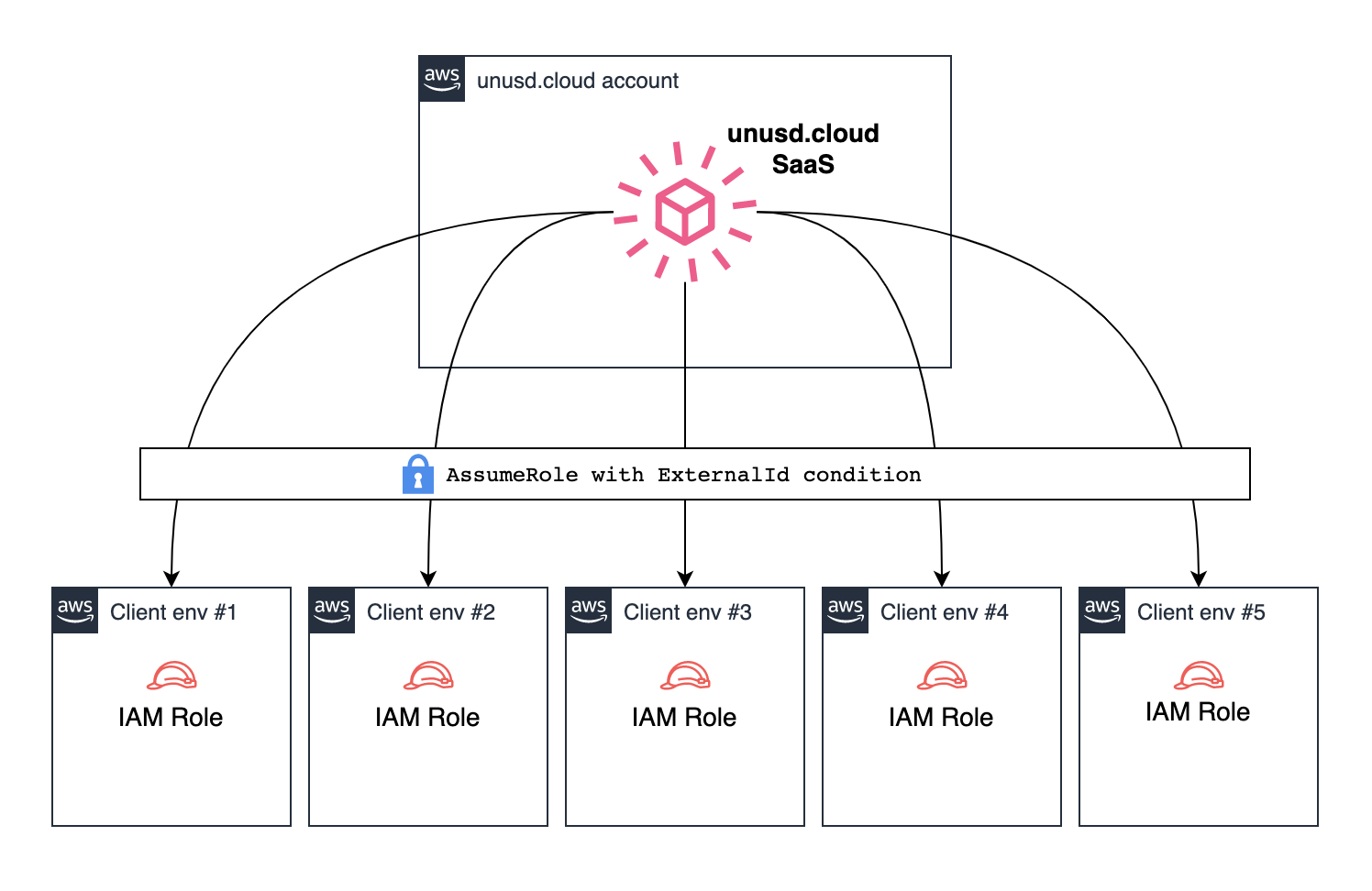
🧙 Hub and Spoke model
Our AWS IAM Role on each of your AWS accounts utilizes the Hub and Spoke model in order to track your unutilized resources and spending information through a few read-only AWS API calls.
The ExternalId or CustomerID employed by the AWS IAM Role is unique to each customer, effectively eliminating the confused deputy problem.
👀 Read-Only Permissions
Our AWS IAM Role is limited to read only actions. We leverage the AWS managed policy SecurityAudit as a baseline, supplemented by a small set of additional read-only permissions required for cost analysis and resource scanning.
AWS Managed Policy
SecurityAudit(arn:aws:iam::aws:policy/SecurityAudit) — AWS-maintained read-only policy covering a broad range of services for security auditing purposes. This policy is managed and kept up-to-date by AWS.
Additional Inline Permissions
The following read-only permissions are not included in the SecurityAudit managed policy and are required for cost analysis, metrics collection, and resource scanning:
💾 Data storage
We do not persist any confidential AWS information. Only metadata configuration items are stored:
- AWS AccountIDs
- Email settings
- Webhooks (Slack / Microsoft Teams) URLs
- Preferred scan schedule
- History of potential savings and wasted resources (Reports)
🔒 Encryption Everywhere
TLS encryption is employed both at-rest and in-transit.