How to Use unusd.cloud with Terraform
This guide provides step-by-step instructions for deploying the read-only permissions required by unusd.cloud to your AWS account using Terraform.
Prerequisites
Before you begin, ensure you have:
- An active unusd.cloud account
- Terraform installed on your local machine
- AWS CLI configured with appropriate credentials
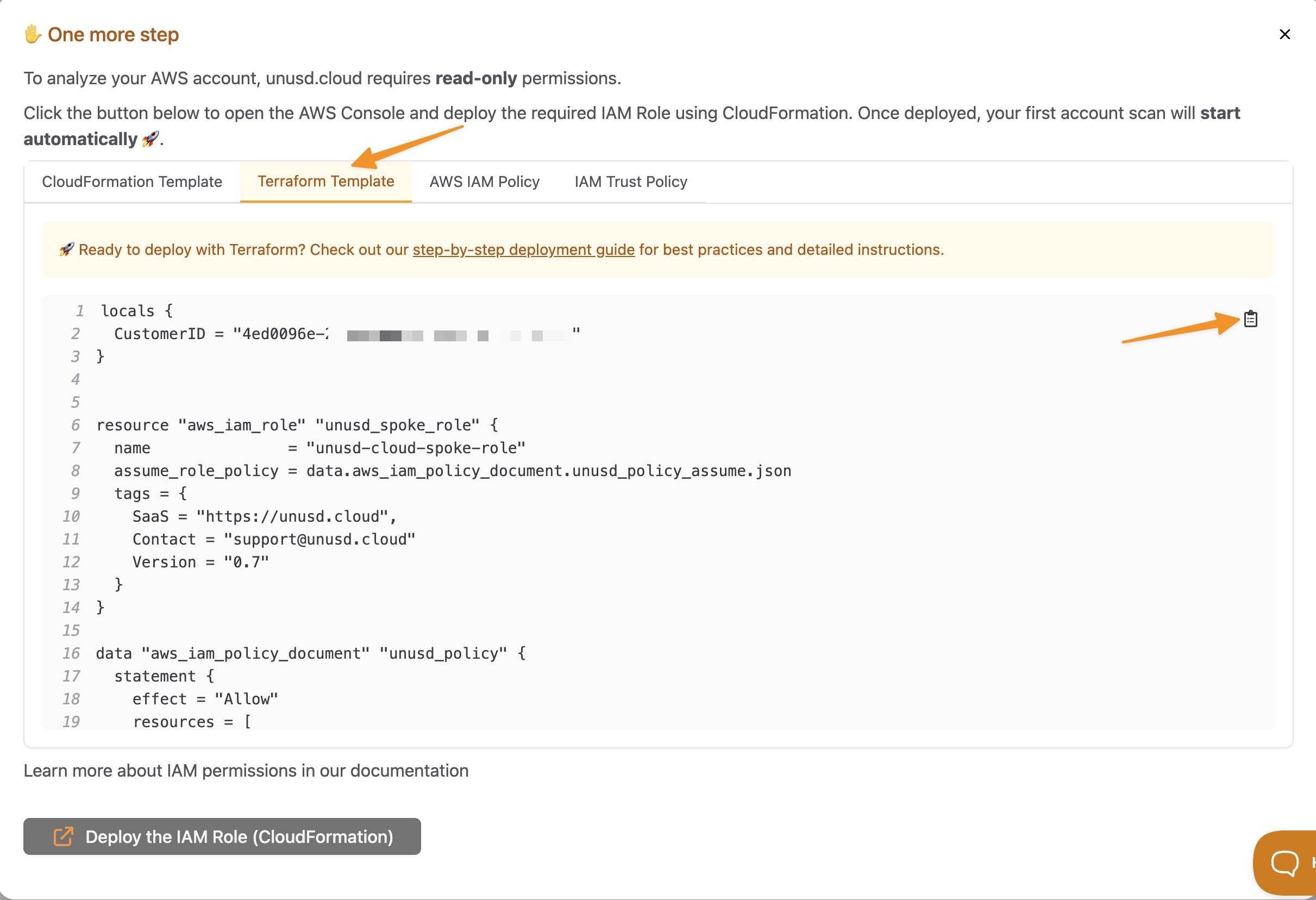
Adding Your First AWS Account
When adding your first AWS account, follow these steps:
- Fill in the required information in the initial modal
- A second modal will appear
- Select the Terraform tab
- Copy the provided Terraform code
Next Steps
With the permissions successfully deployed, you can now:
- Access unusd.cloud's cost optimization features
- Monitor your AWS resources usage (wasted AWS resources)
- Review actionable recommandations to lower your cost and reduce attack surface
Support
If you encounter any issues or have questions about the deployment process, please contact unusd.cloud support for assistance.